ESET has analyzed the Asylum Ambuscade group of cybercriminals, which has been conducting cyberespionage activities since at least 2020. In particular, last year, cybercriminals targeted government officials in several European countries bordering Ukraine.
The goal of the attackers is to steal confidential information and credentials from official government webmail portals.
The Asylum Ambuscade group usually targets small and medium-sized businesses and individuals in North America and Europe.
“Asylum Ambuscade appears to be expanding its activities with recent cyber espionage attacks on government agencies in Central Asia and Europe. It is difficult to track a cybercriminal group that conducts specialized cyberespionage operations, so researchers should keep a close eye on its activities,” explains Mathieu Fau, ESET researcher.
Cyberattack research
In 2022, when the group targeted government officials in several European countries bordering Ukraine, the attack began with an email containing a malicious Excel file or Word document attachment. If the device was of interest to the attackers, they deployed the AHKBOT downloader, which can be extended with plug-ins to track the victim. These plug-ins provide capabilities such as taking screenshots, recording keystrokes, stealing passwords from web browsers, downloading files, and running data-stealing threats.
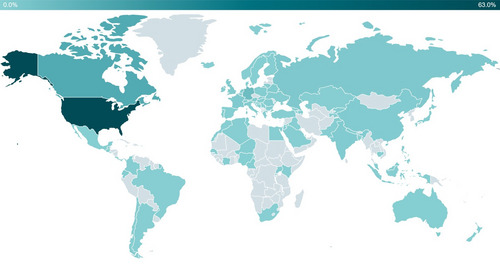
Since January 2022, ESET researchers have counted more than 4,500 victims worldwide. While most of them are located in North America, it should be noted that there have also been victims in Asia, Africa, Europe, and South America. The targets of cybercriminals are mainly individuals, cryptocurrency traders, bank customers, as well as small and medium-sized businesses in various industries.
“The Asylum Ambuscade malware chain is generally quite similar to the one found in previous cyber-espionage attacks. The main difference is the compromise vector, which can be a malicious Google ad that directs to a website with a malicious JavaScript file or multiple HTTP redirects,” the ESET researcher adds.
Due to the danger of attacks, ESET experts recommend following basic cybersecurity rules, including not opening unknown emails and documents, using complex passwords and two-factor authentication, keeping software up to date, and ensuring reliable protection of home devices and corporate networks.